|
|
|
|
|
|
|
|
|
|

 Zoom Zoom
 | Loading… |
|
|
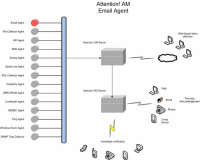
Central point of
consolidation for enterprise alarms
. Inputs are received from a wide variety of systems, applications and devices, providing consistent administration of critcial alarm conditions.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
A
Server / Agent architecture
removes the complexity of interfacing to disparate sources. The Agents speak the language on the input source, passing alarm data to the Server in a consistent format.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
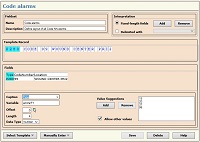
Blueprints of alarm data
are specific to the source of input. Alarm parameters are defined as either a character string, or a number.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
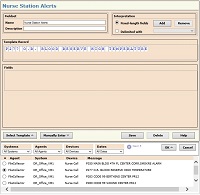
Actual alarm data provides a
template
to define the blueprint for a specific alarm source.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
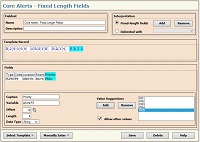
Blueprints for
fixed-length parameters
assign fields based on the character offset of data within the input alarm stream.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
Blueprints for
delimited parameters
assign fields based on a predefined character that separates input alarm data. Typical delimiter characters include commas, semi-colons and tabs.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
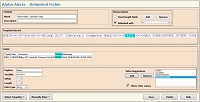
Alarms
for specific data sources are created based on the defined blueprint. Simple relational comparisons for character strings and numbers—equal, not equal, greater than, etc— enable detection of critical input data.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
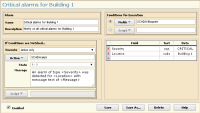
When alarm data comparisons become complex,
alarm processing scripts
are available to address any requirement.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
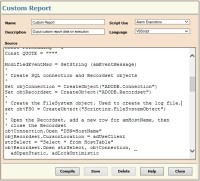
Comprehensive
alarm reporting
delivers insight into enterprise activity. All report data is easily accessed from the browser-based interface.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
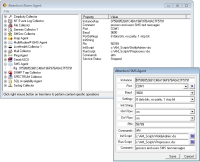
The
SMS Agent
receives SMS text messages from any system, device or person. The contents, and source phone number of the SMS text message are forwarded to the Server for alarm processing.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
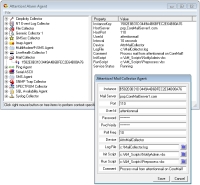
The
Email Agent
receives SMTP email messages from any source. The message body, Subject and From address are forwarded to the Server for alarm processing.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
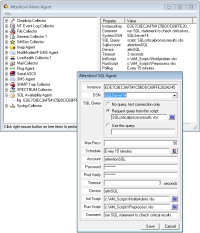
The
SQL Agent
periodically executes a specific SQL command against the desired table. The results of the SQL command—total number of rows, output of a WHERE clause, etc.—are forwarded to the Server for alarm processing.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
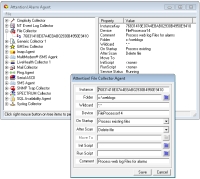
The
File Collector Agent
monitors a specified directory. When new files are written to the directory, every line of the file is transferred to the Server for alarm processing. Most often used to pinpoint significant data within very large log files.
|
|
|
|
|

 Zoom Zoom
 | Loading… |
|
|
The
Serial Line Agent
accepts input from RS-232 connections, then forwards the data to the Server for alarm processing. Typically used to interface with SCADA implementations, and legacy telecom hardware.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
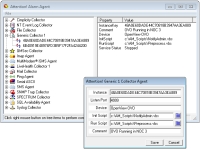
The
API Agent
is the primary interface to management applications. It accepts parameters from a myriad of Operating Systems—Windows, UNIX, Linux, OpenVMS, OS400, MVS—then forwards the data to the Server for alarm processing.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
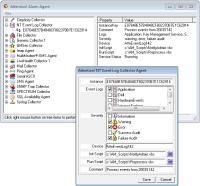
The
Windows Event Log Agent
monitors selected event logs for events of the specified severity. When detected, the log data is forwarded to the Server for alarm processing.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
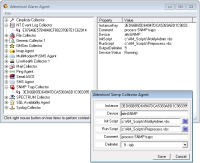
The
SNMP Agent
receives trap data from all sources, then forwards the data to the Server for alarm processing.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
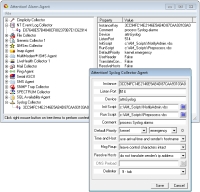
The
Syslog Agent
accepts Syslog messages from all sources, then forwards the data to the Server for alarm processing.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
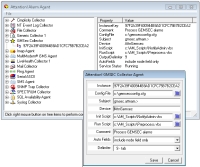
The
GMSEC Agent
is an authorized subscriber on NASA's message bus architecture. GMSEC data is published to the GMSEC Agent, then forwarded to the Server for alarm processing.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
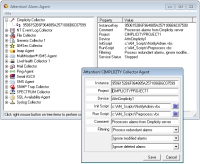
The
Cimplicity Agent
accepts critical SCADA messages from GE Fanuc's Cimplicity automation solution. Messages are then forwarded to the Server for alarm processing.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
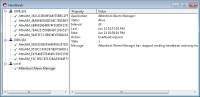
The alarm Server and all Agents implement
heartbeat monitoring
to ensure the monitoring environment is operational, 24 x 7 x 365. Any failure in the monitoring system itself results in immediate notification of designated personnel.
|
|
|
|
|
 Zoom Zoom
 | Loading… |
|
|
High availability configurations provide the
fault tolerance
necessary to make certain every critical alarm message is processed in real time. Redundant Servers and Agents eliminate single points of failure in monitoring architecture
|
|
|